Multiprocessing vs Multithreading
Multi-threaded programs and multi-process systems are the best ways of splitting up workload into multiple actions and partitioning the task into diff...
Read More →We use cookies to improve your experience on our site and to show you personalised advertising. Please read our cookie policy and privacy policy.
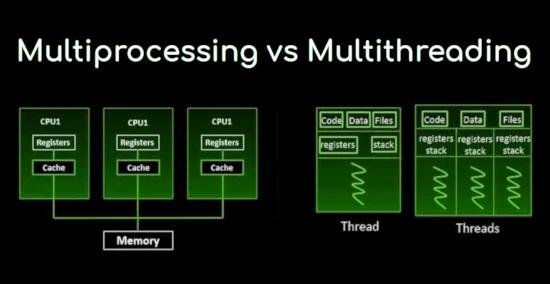
Multi-threaded programs and multi-process systems are the best ways of splitting up workload into multiple actions and partitioning the task into diff...
Read More →
Crime tends to go where the money is, and the money is certainly in e-commerce these days, which is why it should come as no surprise to learn that th...
Read More →
Technology is the cornerstone of modern enterprises as it can help them do things in easier and better ways. Most business owners are willing to inves...
Read More →
In the digital age, distributed denial of service (DDoS) attacks have become a prevalent and concerning form of cyber threat. These attacks can disr...
Read More →
Cyber-attacks and data breaches have become increasingly ubiquitous in recent years. Now more than ever, having cybersecurity tools such as antivirus ...
Read More →
The digital age has brought about numerous conveniences, but it has also given rise to new forms of cybercrime. One of the most prevalent and deceptiv...
Read More →
What is a Computer Cluster?A computer cluster is a single logical unit consisting of multiple computers that are linked through a local area network. ...
Read More →
Using another person’s work and passing it as your own is plagiarism. However, if you understand just enough and paraphrase the same content, it’s con...
Read More →
A VPN is an online security tool that allows you to browse anonymously. Your IP address is an identifier that websites can trace back to you. Using a ...
Read More →
In the realm of cybersecurity, Trojan horse or Trojan is a malicious computer program that is often disguised as legitimate software. It is a program ...
Read More →